According to Data Breach Today, Microsoft has advised of a current email phishing scheme aimed to date at business email customers using “session cookies” to bypass multi-factor authentication (MFA) requirements.
By now we are used to seeing the ubiquitous and required cookies notice (e.g., “Our website uses cookies . . . .”) that pops up when you access a website. [For an explanation of the function of and differences between session, performance, functional, analytics, advertisement, first party, and third party cookies, refer to this CookiesYes article.] Session cookies are temporary cookies generated during each web session which are deleted once the web session ends or you close your browser. Alternatively, session cookies may timeout before the session ends, depending on the particular website (for example, your online banking account website). Far from nefarious, session cookies are necessary to navigate smoothly across a website. For example, session cookies enable you to move back-and-forth among product web pages so you can repeatedly add to your Amazon shopping cart. Eventually, session cookies can capture your checkout information, such as name, address, email address, and credit card numbers. However, because session cookies are not stored on your phone or laptop, a threat actor (TA) is not able to capture that important personal information off your device.
Nevertheless, incompletely described in non-technical and marginally accurate terms, in the current scam once a user clicks on a link in a phishing email, he is re-directed to a proxy server (a phishing site), from which the TA is able to capture the user’s logon credentials and session cookies “that prove [the TA’s] ongoing and authenticated session with the website.” Through this man-in-the-middle (MTM or MITM) attack the TA is eventually able to hijack the session and bypass the authentication requirement. As Microsoft depicts it:
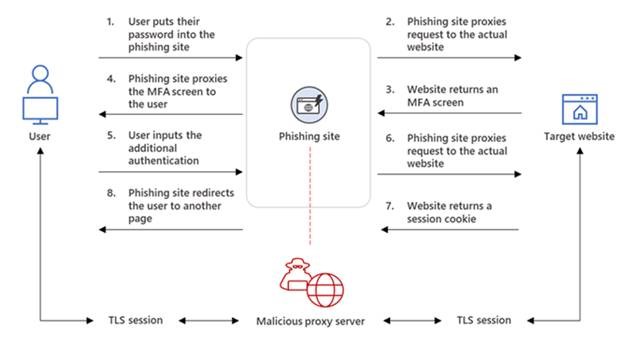
Nonetheless, no matter how ingenious and technologically sophisticated this scheme may be, it all starts with a plebeian (Word of the Day) phishing email. When you receive an email, regardless of how legitimate the email appears, at the very least be extremely cautious before clicking on an embedded link. If you do succumb to temptation, carefully examine the (URL) address of the website where you are sent because the page content and visuals may very closely resemble the website you intended to visit. If something seems not quite right, Google search for the vendor’s true website in a separate tab or, better yet, in a separate browser, and compare the two addresses. If the two don’t fit, you must quit.
 Check out our series, Privacy Perils, to learn what steps you can take to guard your personal and company data. For more information about this topic and other cyber security concerns, please contact a member of our Privacy & Data Security team.
Check out our series, Privacy Perils, to learn what steps you can take to guard your personal and company data. For more information about this topic and other cyber security concerns, please contact a member of our Privacy & Data Security team.


